In this session, we are going to talk about AWS Backup Strategies at rest and in transit.
Two important concepts in AWS Backup Strategies at rest and in transit:
[ads1]
-
Securing Data at rest:
- Server-side encryption and access control
- Data stored in the persistent storage is considered “at rest”
- eg: S3 / Glacier
- Amazon S3 and Glacier can use encryption to protect data at rest
- AWS IAM (Identity and Access Management) can be used to control access to the resource
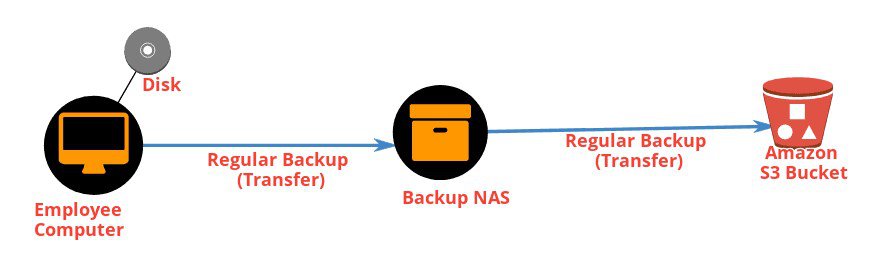
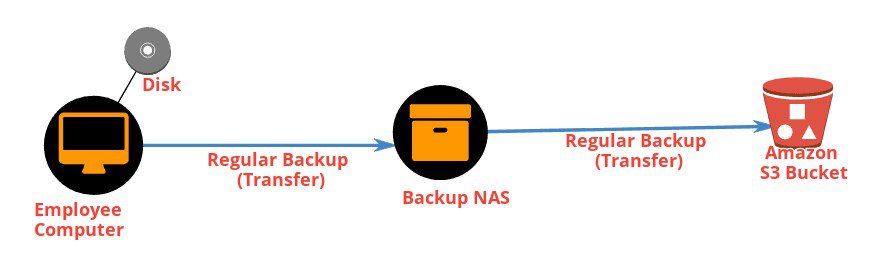
Here is an employee computer and from that computer, it is storing information on the disk. From time to time we perform a regular backup to NAS and it is a central device for saving data, from NAS we regular backup on AWS S3 Bucket.
Our data is at rest all these location computers, NAS and S3 Bucket. We need to secure our data at this location not only in Amazon S3 [ads2]
-
Securing Data in-transit:
- Data needs to be protected while it is being transferred
- Data-in-transit is data flowing through networks
- For example: how can we make requests to Amazon S3 without compromising our keys?
Transferring data can potentially open up to attack, so we also need to look at securing data in transit. [ads3]
Data in transit is data flowing through networks whether those networks are public or private they cannot be trusted for sensitive information instead we need to lookout way for securing data through encryption. But encryption for data in transit is not necessarily the same as in encryption data at rest especially for using data for different keys for encryption from one end to another for this reason it’s important to understand the available options when they make sense and when they don’t make sense. [ads2]
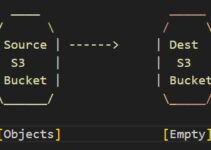
Eg: As shown in the below diagram we focus on data transfer over the network, instead of data at rest. Make sure the data which are transferred over the network is encrypted.
This is the end of this article, AWS Backup Strategies at Rest and in Transit.
[divider style=”normal” top=”20″ bottom=”20″]
Thanks for reading this article, you’ll also like to read below articles.
AWS Disaster Recovery and Fail-over
Oracle Database Security Tutorials