Infrastructure as Code (IaC) has revolutionized infrastructure management, offering automation, consistency, and repeatability. Terraform, a popular IaC tool, excels in defining and provisioning infrastructure resources. However, managing Terraform’s state file, which stores the current state of your infrastructure, is crucial for security and collaboration. This blog explores how leveraging Amazon S3 as a remote backend for your Terraform state strengthens your IaC foundation by providing centralized storage, enhanced security, and streamlined collaboration.
Managing Terraform State File on S3: Centralized Security for Your Infrastructure as Code
Why Leverage S3 for Terraform State Management?
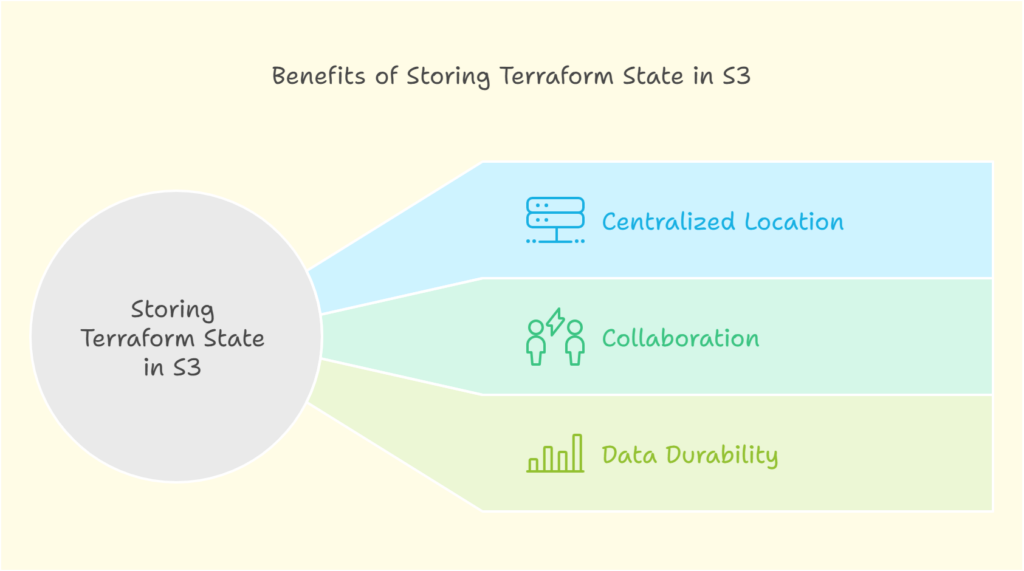
Local state files, while convenient for initial exploration, become unscalable for collaborative projects with growing infrastructure needs. S3, a highly scalable object storage service offered by AWS, provides a robust solution for managing Terraform state files. Here’s how S3 empowers your IaC:
- Centralized Storage: S3 offers a central repository for your Terraform state, accessible by authorized team members, fostering collaboration and efficient deployments.
- Enhanced Security: By storing your Terraform state file in S3, you can separate it from your Terraform configuration files. This segregation reduces the risk of accidental exposure of sensitive infrastructure details.
- Version Control and Rollbacks: S3’s built-in versioning allows you to revert to previous state versions in case of errors or unintended changes, safeguarding your infrastructure.
- Improved Scalability: S3 scales seamlessly with your infrastructure needs, effortlessly accommodating a growing number of resources and state files.
Taking Control: Configuring Terraform State on S3 with Encryption
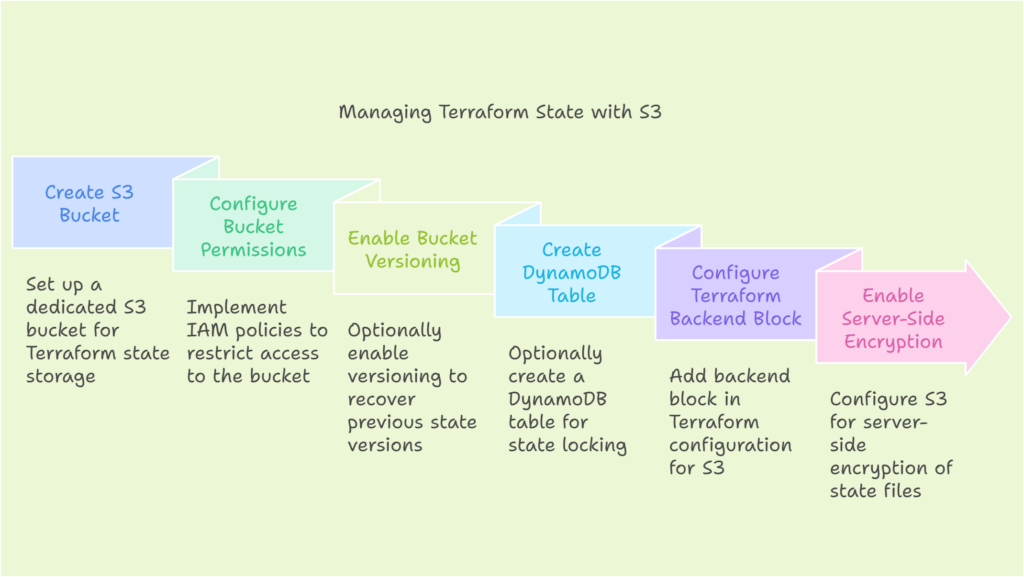
Transitioning your Terraform state to S3 with encryption is a secure approach. Here’s a basic outline:
- Create an S3 Bucket: Use the AWS Management Console or CLI to create a dedicated S3 bucket specifically for storing your Terraform state file.
- Configure Bucket Permissions: Implement IAM policies to restrict access to the S3 bucket. Only authorized users should be able to access and modify the state file.
- Enable Bucket Versioning (Optional): This allows you to recover previous state file versions in case of accidental deletion.
- (Optional) Create a DynamoDB Table: A DynamoDB table with the Terraform S3 backend enables state locking. This helps prevent conflicts when multiple users modify infrastructure simultaneously.
- Configure Terraform Backend Block: In your Terraform configuration file, add a backend block specifying the S3 bucket name, key (path within the bucket), and optionally, the DynamoDB table name.
Here’s an example Terraform configuration with S3 backend and encryption:
backend "s3" {
bucket = "your-s3-bucket-name"
key = "terraform.tfstate"
region = "us-east-1"
# Optional: Use a custom S3 endpoint URL
endpoint = "https://s3.custom-endpoint.com"
# Optional: DynamoDB table for state locking
dynamodb_table = "your-dynamodb-table-name"
}
Enabling Encryption for Added Security
Terraform S3 backend offers built-in support for Server-Side Encryption (SSE) to encrypt your state file at rest. Here’s how to configure it:
1. Modify the Terraform Backend Block
In your Terraform configuration file, add the encrypt option within the backend block and set it to true.
backend "s3" {
bucket = "your-s3-bucket-name"
key = "terraform.tfstate"
region = "us-east-1"
encrypt = true
# Optional: Use a custom S3 endpoint URL
endpoint = "https://s3.custom-endpoint.com"
# Optional: DynamoDB table for state locking
dynamodb_table = "your-dynamodb-table-name"
}
2. AWS Key Management Service (KMS) (Optional)
While Terraform uses SSE-S3 by default with encrypt = true, you can leverage AWS KMS for even stronger encryption. This requires additional configuration steps like creating a KMS key and updating the Terraform backend configuration with the KMS key ID.
Benefits of S3 Backend over Local Storage
Here’s how S3 backend surpasses local storage for managing Terraform state files:
- Collaboration: Enables teams to work together on the same infrastructure configuration.
- Disaster Recovery: S3 offers exceptional durability, protecting your state file from hardware failures and accidental deletion on local machines. S3 replicates your data across multiple availability zones, ensuring high availability and data redundancy.
- Scalability: S3 scales automatically to accommodate your growing infrastructure needs. You won’t need to worry about storage limitations as your infrastructure expands.
- Security: S3 provides a centralized location for your state file, allowing for easier implementation of security measures like IAM policies and encryption. This centralizes control and simplifies security management compared to scattered local copies.
Additional Considerations
- Cost: While S3 offers a free tier for storage and requests, be mindful of potential costs associated with usage exceeding the free tier limits. Pay close attention to the amount of data stored and the frequency of access.
- Performance: Accessing the state file stored in S3 might introduce slight latency compared to local storage. However, for most use cases, this latency is negligible, especially considering the benefits of centralized storage and security.
Advanced Practices for Robust State Management
- Workspace Support: Leverage Terraform workspaces to manage multiple infrastructure environments using the same S3 backend. This allows you to develop and test infrastructure configurations for different environments without affecting the production state. You can explore the official Terraform documentation on workspaces here: https://developer.hashicorp.com/terraform/cloud-docs/workspaces.
- Remote Execution: Utilize Terraform Cloud or Terraform Enterprise for remote execution of Terraform commands. This simplifies state management in complex deployments where infrastructure is provisioned across multiple locations. These managed services often offer additional features like:
- Built-in state locking: Ensures only one user can modify the state file at a time, preventing conflicts during collaboration.
- Enhanced Access Controls: Granular control over who can access and modify infrastructure resources and the state file.
Conclusion
By managing your Terraform state file on S3 with encryption, you gain a secure, centralized, and scalable solution for your IaC workflows. This approach streamlines collaboration, enhances disaster recovery capabilities, and ensures the smooth operation of your infrastructure. Remember to implement best practices like encryption and IAM policies to further safeguard your state file.
Ready to embrace the power of S3 with encryption for Terraform state management? Explore the resources below to get started:
- Terraform documentation on remote backends: https://registry.terraform.io/providers/FlexibleEngineCloud/flexibleengine/latest/docs/guides/remote-state-backend
- AWS documentation on S3 server-side encryption: https://docs.aws.amazon.com/AmazonS3/latest/userguide/serv-side-encryption.html
Additional Resources
- Terraform documentation on workspaces: https://developer.hashicorp.com/terraform/cloud-docs/workspaces
- Terraform Cloud documentation: https://www.terraform.io/cloud
- Terraform Enterprise documentation: https://developer.hashicorp.com/terraform/enterprise
See also:
How to Rename Folders in AWS S3 (The 2 Best Workarounds)
How to Use Terraform to Automate AWS Infrastructure Provisioning
Getting Started with Terraform: A Beginner’s Guide
Terraform vs. CloudFormation: Which One to Choose?
Steps to Install Terraform on Amazon Linux
Setup AWS VPC Peering with Terraform
Copy Objects Between S3 Buckets: A Streamlined Guide
How to Restore Deleted Files in AWS S3: A Step-by-Step Guide
Steps to Install s3cmd on Linux and Manage AWS S3 Bucket
How to Mount S3 Bucket on Linux Instance